How To | Configure TLS support with Avaya Session Manager (SM) for Q-SYS Softphone
Learn how to configure TLS secure communications between Avaya Session Manager and the Q-SYS Softphone.
Procedure
Use the following information to interop with an Avaya system.
Note
Some of this TLS information is provided from Avaya Support.
TLS can be used with Symmetrical or Asymmetrical encryption. SM can use either, or can require certificates from peers (Asymmetrical) for more secure connections. For Asymmetrical, this a setting in SMGR for each SM’s Entity Link properties. For Q-SYS, use "Trusted". (Q-SYS does not support loading certificates.)
Note
When configuring SM for Q-SYS, use TLS\5061 instead of UDP\5060 from the screenshot.
SM 8.x defaults to TLS 1.3 only, but can be set to support older TLS versions for compatibility. This is an SM property setting. Q-SYS supports 1.2 and below.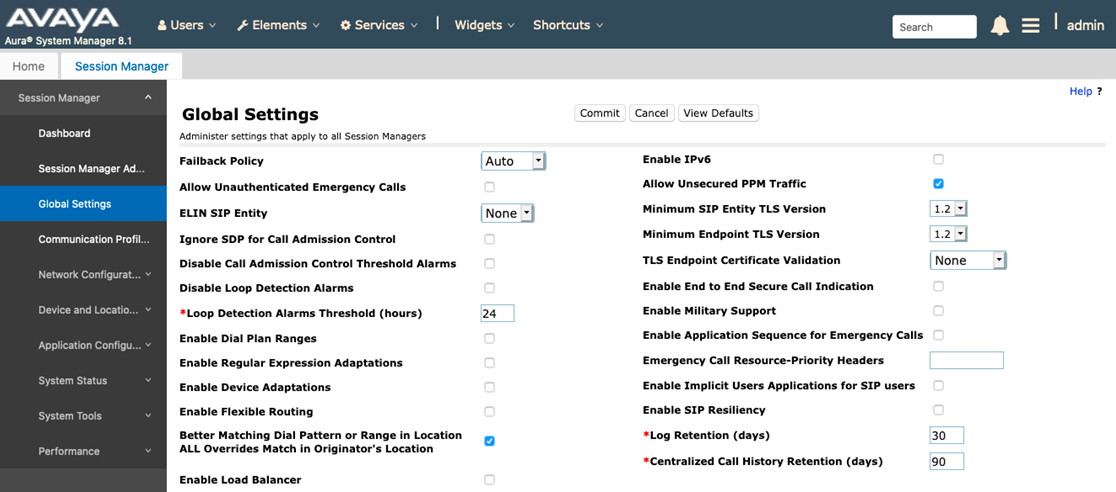
Since Q-SYS doesn’t use the SMGR CA, but rather “blind trusts” the SM ID Cert (our phones typically do this too), the handshake looks like this:
- Client (QSC) Hello (without cert) containing supported algorithms > SM
- SM (by virtue of being instructed to “trust” the QSC entity sends its ID Cert in a Server Hello with an acceptable mutually agreeable algorithm > QSC.
From this point, SM generates a shared key and cyclical algorithm to Q-SYS and both will use the shared key for TLS-encrypted messages. SM will revert to the shared key if it is instructed to trust the entity, and if no ID cert is presented.